
Warning of Increased Risk of Ransomware Attacks on Educational Institutions
The National Cyber Security Centre SK-CERT (hereinafter referred to as “NCKB SK-CERT”) warns of an increased risk of ransomware attacks by the Medusa group, which are particularly targeted on educational institutions. A successful attack will cause a total unavailability of systems and services and a leak of sensitive information.
What is the Medusa group?
According to the information available, the Medusa group appeared in 2021 but had relatively very low activity. Medusa gained the security community attention after an attack on the Minneapolis Public Schools district in March 2023, from which it demanded a ransom of 1 million dollars for non-disclosure of data. It attacks various types of targets, including healthcare facilities, the manufacturing sector, financial institutions, and so on. However, educational institutions (universities, primary and secondary schools, scientific institutions) have the highest percentage, both in terms of number of institutions and in the amount of the ransom.
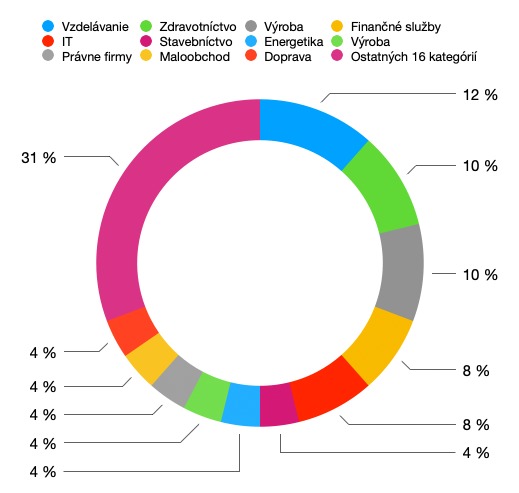
Source: NCKB SK-CERT
The Medusa group can be easily confused, as the word “Medusa” is used by several different threat actors in cyberspace – there is, for example, the Medusa botnet, the MedusaLocker ransomware or the Medusa Android malware. These are different groups of threat actors, which are not interrelated. However, the Medusa group uses specific techniques, tactics and procedures by which an attack can be attributed.
The group focuses on the so-called double-extortion strategy, i.e. after infecting the victim with the ransomware, the attackers first steal the data, then encrypt them and then demand a ransom. The group runs its own blog on the dark web, through which it provides information to its victims. On the blog, you can see a timeline with the date of the attack, the name of the victim, the amount of the ransom, and a countdown that shows how much time is left until the data is released. However, even this time does not guarantee anything for the victim. In fact, while the victim is running out of time to pay, anyone can buy the data for the same amount as is the ransom currently demanded.
If the victim has not paid the ransom, the timeline will show the victim’s data in green with a “PUBLISHED” flag indicating that the victim’s data has already been published. It can be searched on the blog and contains links to Twitter groups and their Telegram channel as well.
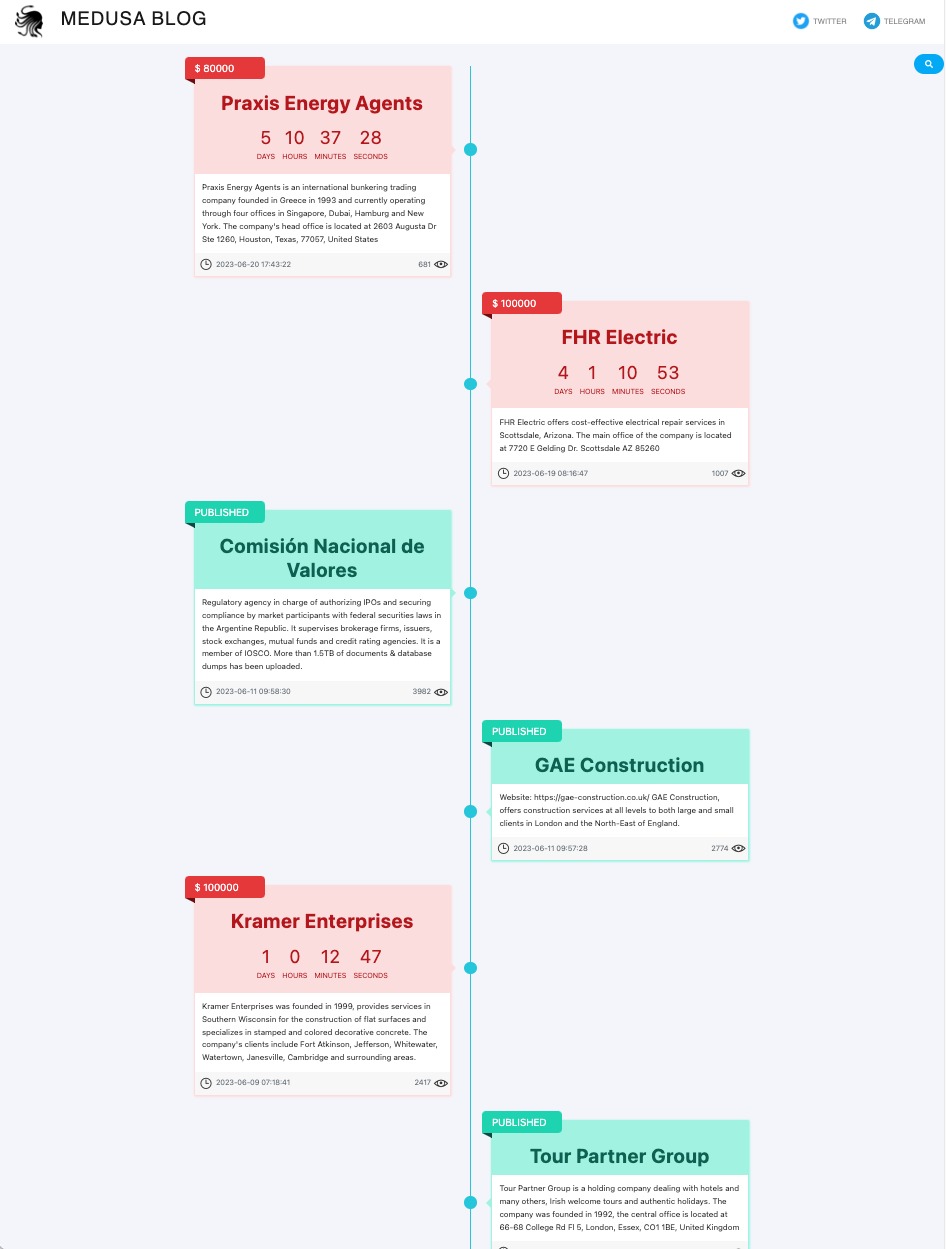
Source: NCKB SK-CERT, captured on 23 June 2023 at 09.05 a.m.
The targets of the Medusa group are not geographically limited. This year, Medusa has attacked targets in various countries (e.g. in Singapore, Kenya, USA, Australia, Cyprus, Portugal and elsewhere). By analysing this group, it can be assumed that it is a criminal group focused on financial profit, and probably originating from Russia. The exact organizational structure of this group or the expertise of its members is not yet known.
How does the Medusa attack work?
As with other existing ransomware groups, live people are behind the main part of the attack. So you are not fighting against ransomware software, but against a sophisticated attacker who tailors his activity to the current situation. The group chooses its victims according to several factors that are currently not publicly known.
Attackers infiltrate the system, probably mainly through compromised login credentials (obtained through phishing, dark web purchase, or brute force attacks on infrastructure access channels – e.g. RDP or otherwise). Subsequently, after infiltrating the infrastructure, the attackers perform the analysis of the infrastructure and the available data, exfiltrate the data by using various methods, try to infiltrate other parts of the infrastructure, monitor data flows and so on. There is no information on how much time the Medusa group spends in this stage. After obtaining the necessary data, the attackers in the compromised infrastructure will deploy the ransomware (encryption) software on each target device separately as the last stage of the attack. The ransomware itself does not establish network connections and does not contain the functionality for independent dissemination through the network, which reduces the opportunity to intercept the encryption process by network detection.
The ransomware is intended for devices with Windows and Linux operating systems. Encryption is performed uniquely on each target device. Technical analysis has shown that the so-called ransom note along with the public encryption key are thus unique for each compromised device in the infrastructure. This makes detection difficult, for example through the identification of the malicious code hashes, and also the decryption itself, as each infected device requires a unique decryption key. The ransomware does not encrypt entire files, but several parts of them, which significantly speeds up the encryption process itself. This allows a large number of files to be encrypted in a short time, so even if you find out soon enough that the ransomware is encrypting data, it is often already too late.
Once the ransomware is deployed in the compromised infrastructure, it shuts down various services and processes, including security software and virtualization services prior to encrypting the data. In the case of the Windows operating system, malicious code deletes Shadow Volume copies, making it difficult to recover the data later. It also focuses on deleting local files that are related to backups as well as on deleting virtual hard drives. These files are deleted before the encryption itself:
*.VHD, *.bac, *.bak, *.wbcat, *.bkf, Backup*.*, backup*.*, *.set, *.win, *.dsk
The ransomware encrypts the data using AES-256 and RSA-2048 encryption. It uses the BCrypt library. There is currently no freely available decryption tool that could decrypt the encrypted data. Encrypted files have the .MEDUSA extension (e.g. document.doc.MEDUSA).
The ransomware creates a !!!READ_ME_MEDUSA!!!.txt file in each folder that contains encrypted files, including a note from the attacker. The note informs the victim of what has happened and what to do in order to get access to their data and to prevent them from being published.
After the encryption is finished, the ransomware deletes itself, which complicates both the data analysis and the data recovery. It is important to provide a sample of the malicious code for the analytical workplace that handles cybersecurity incidents. It can contribute to a better analysis of the entire attack.
Recommendations
The National Cyber Security Centre SK-CERT recommends that all organizations take the following measures:
- minimize or completely disable remote access to your network and systems, and if such access is necessary, monitor remote access, limit remote user privileges, and use a VPN with multi-factor authentication for remote access;
- do not make remote access services such as RDP, SSH, VNC, telnet, etc. available directly on the Internet;
- increase your monitoring attention by focusing on non-standard and unexpected activities, monitoring remote access to your network and network activities. We recommend that such monitoring should operate in a 24/7 mode;
- disable all ports and protocols that are not necessary for the operation of networks, systems and services;
- map all public services of your organization exposed to the Internet and then:
- completely shut down unnecessary and unused systems,
- update outdated systems,
- review accounts and password policies on systems accessible from the Internet,
- delete old accounts;
- secure your email systems using various security methods (e.g. SPF and DKIM, anti-spam filters). Configure a mail server so that malicious and suspicious emails do not reach users’ mailboxes;
- check the effectiveness of your backup system, update your backup procedures using the 3-2-1 rule;
- review your backup policy, verify the validity of your backups and make sure you have at least one latest offline backup. The backup system should be password- and technologically independent from the rest of your infrastructure;
- check and update your access management, remove all old and unused accounts, restrict access of individual users according to the “need to know” rule;
- update your password policy so that the use of the same password for different services is prohibited and the use of strong passwords or passphrases is enforced. This measure needs to be implemented not only from a procedural point of view, but also from a technical point of view;
- implement and enforce multi-factor authentication, including email and VPN services. We recommend avoiding SMS authentication. Use authentication methods that are resistant to social engineering (e.g. physical tokens);
- review the software and firmware update policy and immediately update all systems and services, especially with security patches. Perform vulnerability scans with available tools to determine the extent of vulnerable systems;
- scenarios and procedures that will be applicable to mentioned types of situations include in business continuity plans;
- educate your employees about the risks of cybersecurity incidents and inform them about the increased risk of attacks. Perform targeted educational activities according to the roles and responsibilities of individual employees:
- ordinary users – principles of social engineering and how to prevent them,
- administrators – secure infrastructure rules,
- cybersecurity experts – specialized security training;
- repeat the training (depending on the role of each user) on a regular basis;
- conduct phishing tests and cybersecurity exercises (blue vs. red team, tabletop) on a regular basis.
If you experience a cybersecurity incident such as ransomware:
- immediately contact NCKB SK-CERT and communicate with them during incident handling;
- block or change all access passwords that allow remote access directly or via VPN;
- store digital traces, logs of server, desktops, network devices, disk and memory images, snapshots of virtualized devices safely. Only after this action, proceed to do reinstallation and data recovery attempts;
- identify from which parts of the network and what data have been leaked and try to minimize the impact, for example:
- by changing access credentials to services that may have been leaked,
- by disabling services that an attacker could have accessed due to a data leak;
- anticipate a compromise by a real attacker, not just malware, and adapt your service recovery strategy accordingly. Regarding the service recovery, give priority to complete reinstallation of the infrastructure with minimal and strictly controlled data transfer from the original infrastructure.
Sources
https://resources.securityscorecard.com/research/a-deep-dive-into-medusa-ransomware
https://blog.cybercx.com.au/holding-a-mirror-to-medusa
https://www.techradar.com/news/the-medusa-ransomware-group-is-getting-serious
« Späť na zoznam





