
URGENT: Warning against fraud abusing the identity of tercio.sk
URGENT: Warning against fraud abusing the identity of tercio.sk
The National Cyber Security Centre SK-CERT (hereinafter referred to as SK-CERT) warns against fraudulent e-mails designed to give the impression that their sender is the operator of the Internet store tercio.sk. The e-mail promises a refund.
Based on SK-CERT activities and in cooperation with partners, it was found out that this phishing campaign is intensive in Slovakia and the number of victims is constantly increasing.
This is a large-scale phishing campaign. Its principle is to give the impression that the recipient of the e-mail is to receive a refund from the operator of tercio.sk. However, this is not based on truth and the real aim of the campaign is to lure the victim into providing their personal data and payment card numbers as well as an unauthorised payment.
In terms of technical design and modus operandi, this is a very similar phishing campaign as it was recently conducted in order to abuse the identity of the Financial Administration. We therefore ask citizens not to respond to such e-mails.
SK-CERT in relation to this campaign and also other phishing campaigns RECOMMENDS the following:
- Follow the basic principles of cyber hygiene
- do not open unverified messages and messages from unknown users;
- do not open suspicious attachments (even in familiar formats such as .pdf/.docx and so on);
- disable macros in documents;
- do not open suspicious URLs;
- if e-mail applications are used, disable the attachments preview function;
- in case of suspicion, verify the content of the message with the sender in a different way (by phone, in person);
- never respond to messages requesting any personal and sensitive information (login names, passwords, payment details).
- Never log into any service directly from the URL received by an e-mail and be more cautious. If the URL address does not match in full with an official URL address, it can be a malicious website. When logging into services, use trusted URL links from websites of service providers.
- Under no circumstances should you enter your personal/login information on websites that are anyhow suspicious or have no reason to request similar information.
- Keep your devices updated, not only the operating system itself but also all software components.
How the attack is executed?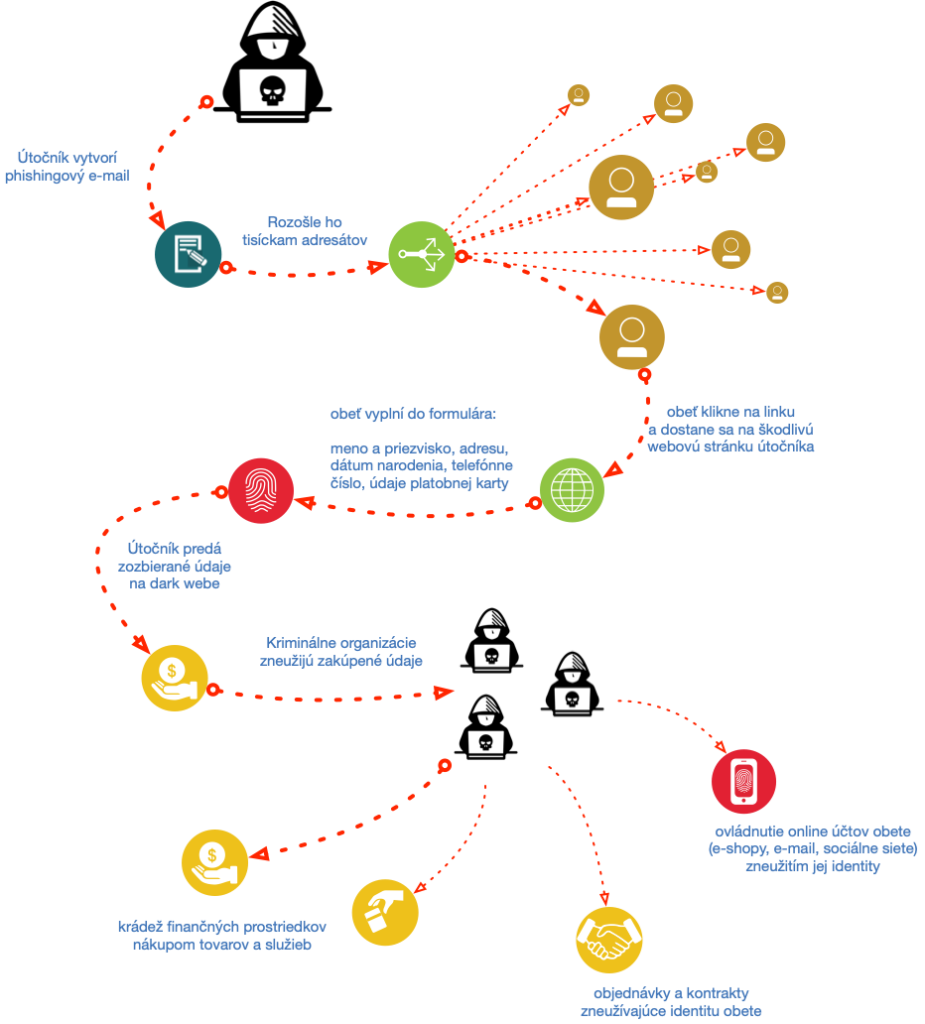
An example of a fake webpage
In this phishing campaign, fake pages are hosted on different URL addresses:
hXXps://www.ristoranteladarsenagrado[.]it/wp-content/upgrade/httpswww.tercio.sk
hXXps://www.ristoranteladarsenagrado[.]it/wp-includes/httpswww.tercio.sk
However, the attacker may own other domains from which the attack is executed.
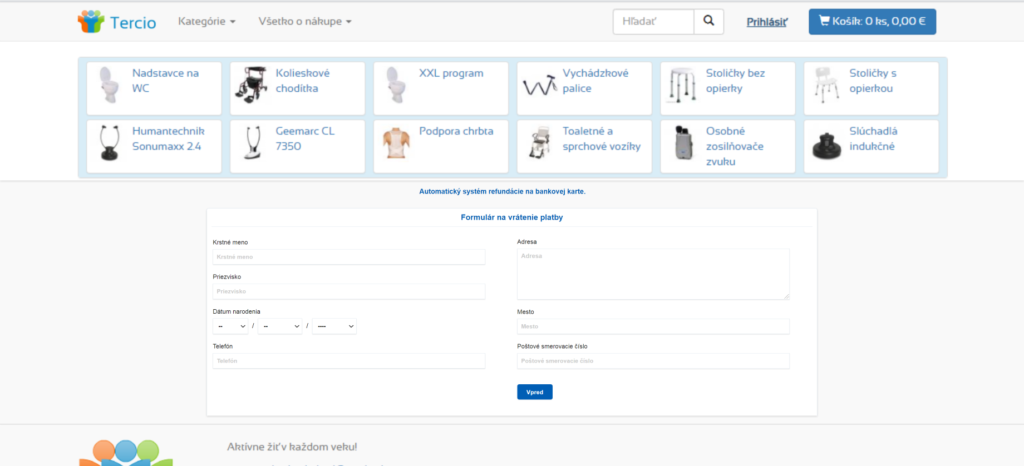
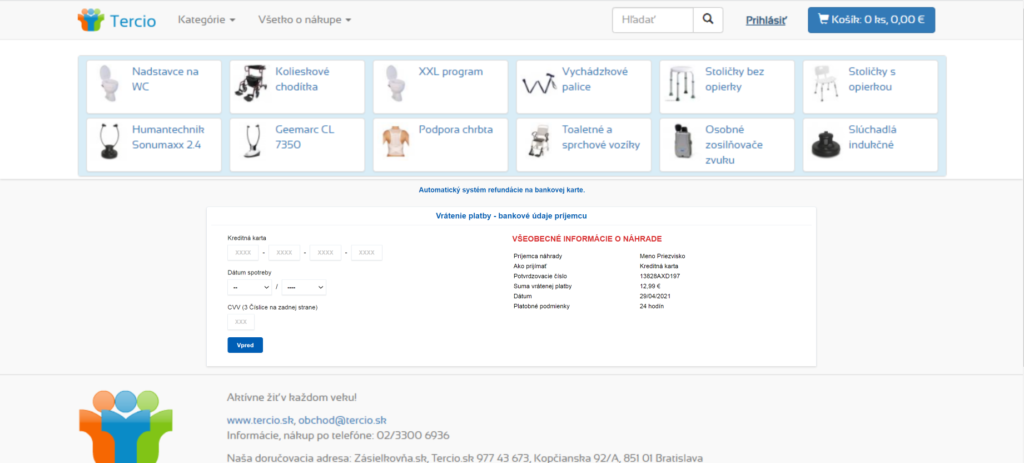
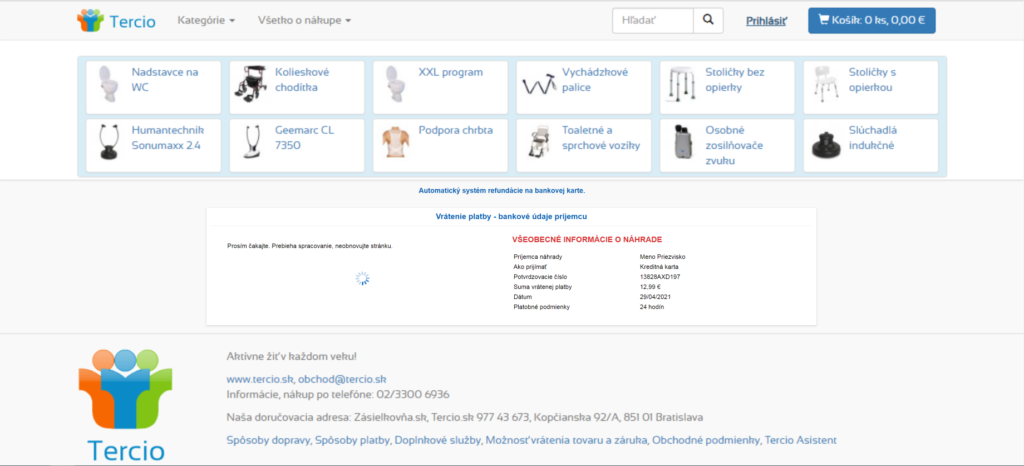
Under no circumstances should you visit this page and fill in anything. A malicious page looks as follows (there are also attached images of successive steps on the page):
1.
2.
3.
4.
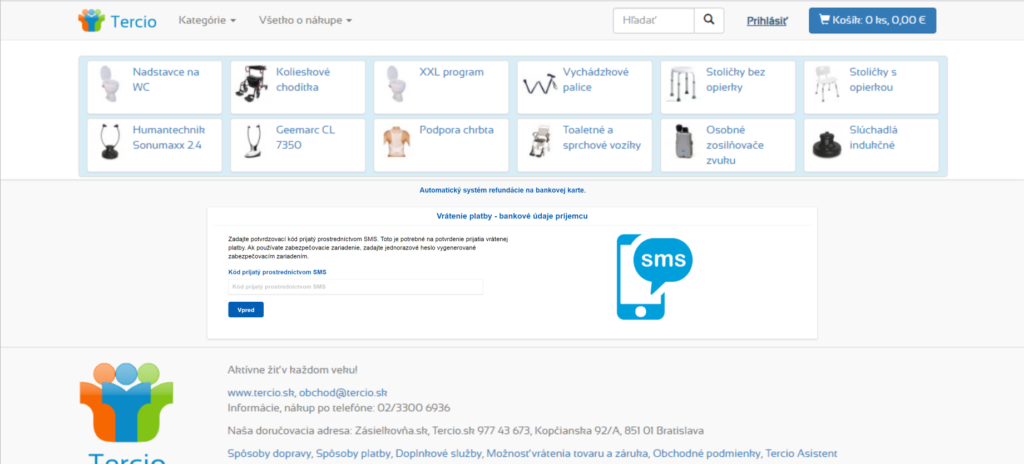
5.
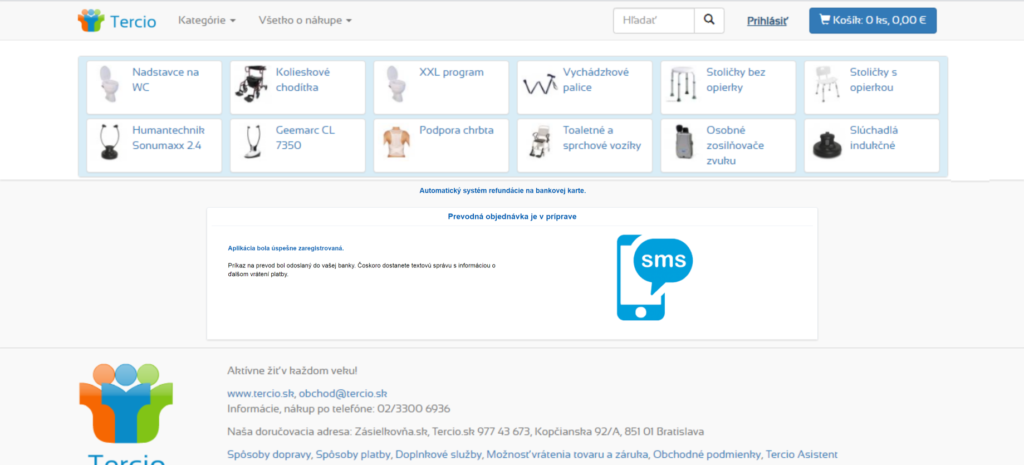
« Späť na zoznam





