
National Cyber Security Centre SK-CERT warns against ongoing harmful activities related to COVID-19
As reported in a previous warning on February 27, 2020 attackers are trying to exploit the situation where people are afraid and uncertain about the spread of COVID-19. In such situations, people are prone to believe various and false reports about COVID-19 and thus have a reduced ability to detect harmful content.
The National Cyber Security Center SK-CERT warns against ongoing harmful activities in cyberspace, which develop over time as follows:
Suspicious online stores
A number of suspicious online shops have been identified to offer limited goods such as masks, respirators, or other protective equipment. The site appears to be legitimate, hovever lacks any business information about the service operator. These websites collect information from the user, such as name, email address, physical address, and phone. Please note that this may be an attempt to collect personal and sensitive information, and the goods ordered by the user may not be delivered. We recommend that you verify the seller’s reputation before making any online purchase. If you have any suspicion, please do not enter payment or other sensitive information on the page.
Malicious apps and COVID- 19 themed domains
A recent form of attack is targeting those users searching for cartographic data on the spread of COVID-19. Attackers are trying to force a user to download an application that does not require installation. Application displays a live COVID-19 spread map. The application uses a malicious code, known as AZORult (known since 2016), which collects information stored in web browsers such as cookies, browsing history, login details, credit card numbers and other sensitive data.
This malicious website is stealing a design and the graphics of live map used by John Hopkins University. However, a fake page is placed on a completely different domain:
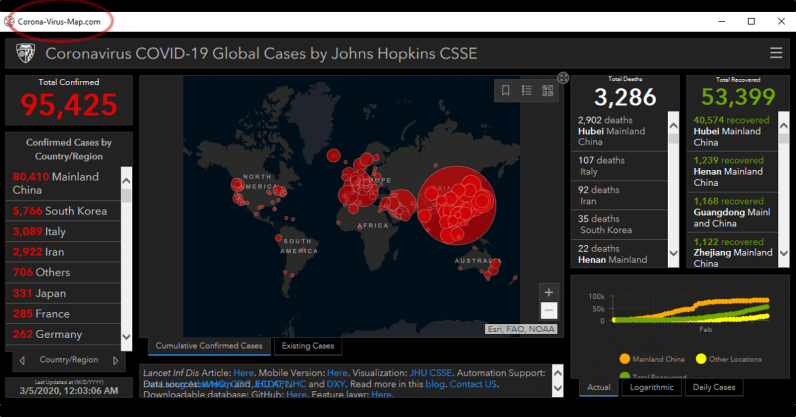
It should be noted that the above-mentioned online corona virus case live map created by Johns Hopkins University in Maryland, USA, is not infected in any way and is safe to visit at this link: https://www.arcgis.com/apps/opsdashboard/index .html # / bda7594740fd40299423467b48e9ecf6
Currently, only Windows computers are affected, however attackers are expected to continue to exploit the situation and work on new alternatives that could affect other systems.
More than 4000 COVID-19 related domains
Since the beginning of 2020, more than 4,000 domains have been recorded that are directly related to the corona virus. Up to 3 percent of these domains were defined as malicious, another 5 percent as suspicious. [1] Such domains include:
- coronavirusstatus [.] space
- coronavirus-map [.] com
- canalcero [.] Digital
- coronavirus [.] zone
- coronavirus-realtime [.] com
- coronavirus [.] app
- coronavirusaware [.] xyz
- coronavirusaware [.] xyz
- corona virus [.] healthcare
- survivecoronavirus [.] org
- vaccine-coronavirus [.] com
- coronavirus [.] cc
- coronavirusupdate [.] tk
- bestcoronavirusprotect [.] tk
Ongoing phishing campaigns
The attackers continue to spread phishing emails that exploit the situation of COVID-19 spreading. They use various forms of social engineering to lure sensitive data from the victim.
Emails with medical advice
This campaign is based on distributing emails that contain an attachment or a download link. The text of the email is very simple and invites the recipient to download the attachment or click on the link for information on precautions to prevent the spread of COVID-19. They refer to the Chinese experts who were supposed to issue these measures. The attachment, as well as the link, contains malicious code.
In addition, these emails may also offers functional vaccines or medicines to cure the virus. Currently, there is no evidence of effective drug or vaccine for COVID-19, this is in effort to lure the victims.
Company mails with instructions
There is a widespread campaign that exploits people’s trust in their employer. The emails link to the new policy connected to the spread of the disease. The link brings you to a malicious domain, and when the user clicks the link, the user downloads the malware.
Emails from official institutions
Emails designed to misrepresent themselves as official institutions such as the World Health Organization (WHO) or the Centers for Disease Control and Prevention (CDC) are designed get user confidence, however, they contain malicious attachments or links to malicious websites.
Abuse of solidarity
We have also received reports in recent weeks for attackers calling on individuals to help victims financially in areas affected by COVID-19. Attackers request a cryptographic transfer as a form of payment. The attackers’ position is that the money is intended to spread a vaccine that does not yet exist.
Recommended actions
The National Cyber Security Center SK-CERT issues the following recommendations regarding harmful activities that exploit the spread of the COVID-19 virus:
- Always check the legitimacy of emails or other message (SMS, social networking, other online services, etc.) – for example, in person or by phone. If the email originates from an official institution or authority, check the email address or person listed to see if they even exist or if it is the official address or person´s representing the institution.
- Be aware if the message you are reading contains grammatical errors – this may be an automated translation that is often used by attackers
- Do not open messages from unverified or completely unknown senders that contain a suspicious message subject
- Do not open or download suspicious attachments or links in emails
- Turn off the attachment preview feature in your email settings
- Do not respond to messages
- that ask you for sensitive information – login information, personal information, credit card information
- prompting you to act now – provide your personal or other sensitive information, to click a link, or download an attachment
- that offer guaranteed functional vaccines or medicines – there is no treatment or vaccine for COVID-19 at this time
- calling for donations to victims through cryptocurrencies – official collections are legitimately identified and do not use payment in cryptocurrencies
- Use trusted sources to find out about COVID-19 – official institutions such as the Ministry of Health of the SR, Public Health Office, World Health Organization, or other legitimate research institutes sites.
- Shop only from verified online stores. National Cyber Sercurity Centre SK-CERT have provided recommendations for online shoping: https://www.sk-cert.sk/en/advices-regarding-shopping-on-black-friday-and-cyber-monday/index.html
- For up-to-date information on COVID-19, please visit the official website: https://www.korona.gov.sk/. On this page are also all important contacts: https://www.korona.gov.sk/dolezite-kontakty/
Sources:
[1] https://blog.checkpoint.com/2020/03/05/update-coronavirus-themed-domains-50-more-likely-to-be-malicious-than-other-domains/
https://www.recordedfuture.com/coronavirus-panic-exploit/
« Späť na zoznam





