
Ransomware and its reality today
It is certainly not necessary to explain again what ransomware is. In short, it is a malicious activity that leads to encryption of data (disks, and with poorly designed infrastructure even of backups if they exist). Subsequently, the attacker blackmails the victim and asks to pay a certain amount (so-called ransom) most often in bitcoins or other untraceable cryptocurrency as a condition for data decryption.
No one can actually count the number of such attacks in the world. According to one of the reports, the average ransom in 2020 in the US was around $ 312,493, which is a 311 % increase over the year 2019. At the same time, the report shows that the average downtime of ransomware-infected companies is 21 days (Coveware) and the average number of days for victims to fully recover from the attack is 281 days (Emisoft). In 2020, around 2,400 ransomware attacks hit large companies in the US alone. According to another report (from Sophos), on average, 50 % of organisations in the world have already become the victim of ransomware. Of the total number of victims, on average, 26 % of organizations paid the ransom. The average cost of ransom paid for organizations of 100 to 1,000 employees was $ 505,827 and for organizations of 1,000 to 5,000 employees was $ 981,140.
The most common route of attackers to the victim’s infrastructure is via a malicious file download or an e-mail with a malicious link (29 % of cases), a direct attack on a poorly secured server (21 %), an e-mail with a malicious attachment (16 %), misconfigured cloud instances (9 %), RDP (Remote Desktop Protocol, 9%) or via a supplier (9 %).
Today, ransomware is considered to be one of the biggest threats for our computers and the data within. A number of countries (including Slovakia) treat it as a national security problem, as it often results (in addition to financial loss) in the failure of a large part of the infrastructure, including the infrastructure of critical enterprises (i.e. enterprises with critical services for the state and citizens). And it is becoming more common and more dangerous.
The target of hackers ranges from a simple computer in your house (with a ransom in hundreds or a few thousand euros) to large companies, manufacturing companies or service providers in critical infrastructure. Among the latest (and internationally publicized) cases belong, for example, a ransomware attack on Colonial Pipeline, the operator of the 8,900 km key pipeline, usually carrying 2.5 million barrels a day on the East Coast of the US.
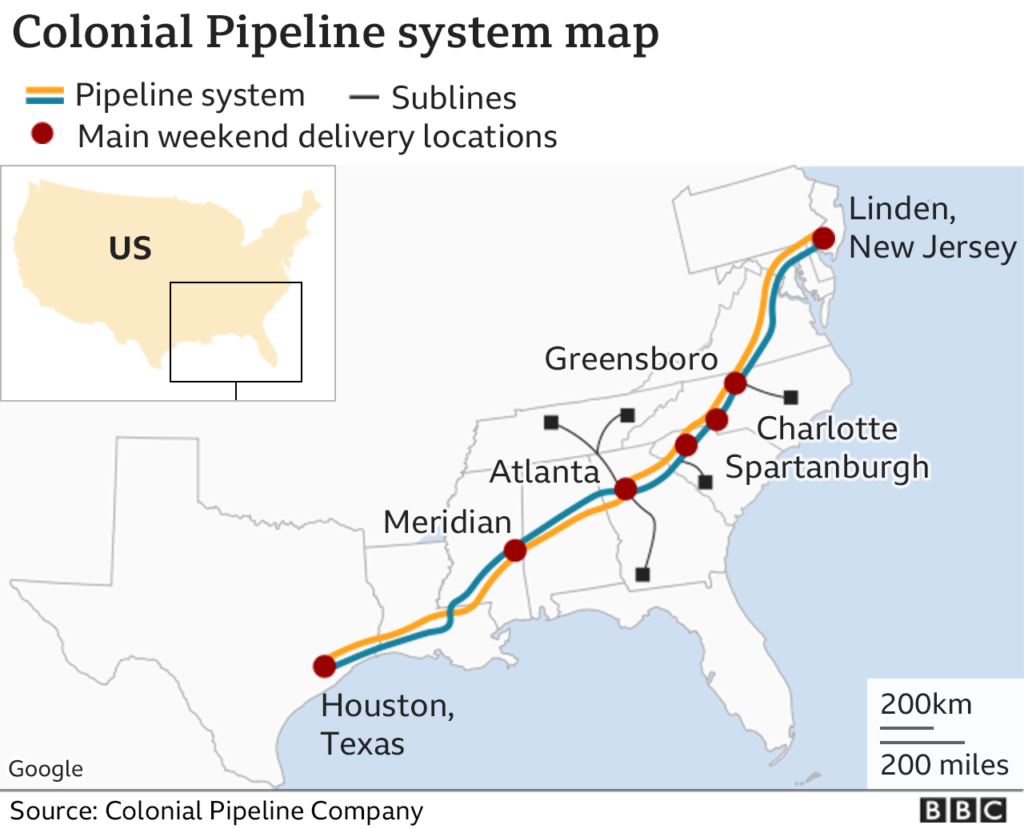
Along with the encryption of the company’s key systems, the attackers stole almost 100 GB of data. The FBI confirmed that a gang previously identified as DarkSide was behind the attack, and demanded nearly $5 million in ransom. According to current information, Colonial Pipeline paid the ransom in order to be able to resume operations of the pipeline, the failure of which could paralyse a significant part of the industrial East Coast of the US.
A similar attack from the same attacker DarkSide was executed just a few days ago in nearby Germany. Chemical distribution company Brenntag paid a $ 4.4 million ransom in Bitcoin to the DarkSide gang. Brenntag is a world-leading chemical distribution company with over 17,000 employees worldwide at over 670 sites in 77 countries around the world including the branch in Slovakia. More than 150 GB of data was stolen during the attack and Brenntag wanted to prevent their leakage.
The last known attack is from Friday 14 May 2021. One week after the US pipeline attack, the Irish Health Service Executive (HSE) said that following a significant ransomware attack, it shut down all its computer systems for preventive reasons. HSE announced that the attack was executed by a criminal group using an adapted “Conti” ransomware tool. As one of the results, many patients received direct e-mails with the threat that if they did not pay, their personal health information would appear on the Internet.
We have such cases in Slovakia as well. The number of ransomware attacks is constantly increasing. Organisations reporting these attacks to the National Cyber Security Centre SK-CERT are also increasing (this is an obligation for operators of essential services under the Cybersecurity Act, for others it is recommended). There are also cases in Slovakia where a ransom was demanded in the amount of hundreds of thousands of euros and where such ransom was paid. So, this issue is not distant and concerns us as well.
The National Cyber Security Centre SK-CERT has therefore warned many times about this danger. Warnings and recommendations can be found in the articles here, here, here or here.
Sources:
The State of Ransomware 2020 (Sophos)
« Späť na zoznam





