Concepts and Standards for Cybersecurity of OT Systems
This part serves as a basic recommendation for all operators of essential services operating industrial devices.
Different institutions around the world are looking for effective cybersecurity measures of industrial OT systems. Individual concepts have their historical evolution, differ according to place and time of their origin and approach the solution of cybersecurity from different points of view. Institutions such as NIST, NERC, ANSI/ISA and others that covered mainly national or regional competence (USA, Canada, Mexico,…), were the pioneers therein.
Cyber threats are constantly evolving and introduce new ways of attacks. Statistics of cyber incidents clearly confirm that about 20% of attacks are coming from “the outside” of systems and about 80% of attacks are from “the inside” of systems. Actions based on organizational measures and the “human factor” appear to provide only partial and less effective cybersecurity for OT systems.
While in the past it was sufficient to implement organizational and procedural measures combined with simple technical solutions (e. g. Firewall on the system perimeter for the network separation, login/password or communication monitoring) to achieve cybersecurity, however, today such measures are no longer satisfactory.
Reliable and proven cybersecurity measures are currently introduced in a multi-level “defense-in-depth” concept implemented in each individual device (an end device) as well as at the system level. Particular functions of active defense-in-depth cybersecurity must be implemented at hardware level and end-device operating system level.
This concept has arisen from the team work of several European users and operators of critical infrastructure systems in order to define requirements, measures and mechanisms for effective cybersecurity solutions today and also with future perspective.
At present, the defense-in-depth concept is supported by reputable manufacturers of OT devices and is implemented in European companies operating energy systems.
This concept is a part of the following recommended standards:
- IEC 62443 a guidance on industrial automation and control systems
- BDEW White Paper a recommended directive for control systems of energy devices
A historical overview of institutions and standards dealing with cybersecurity in chronological order:
NIST (The National Institute of Standards and Technology), since 1988, regional/national competence in the USA, non-governmental scientific laboratory of the U.S. Department of Commerce, focusing on information technology and information protection
Recommendation: Use for informational purposes only to address cybersecurity of OT systems in the EU.
NERC (The North American Electric Reliability Corporation), since 2006, regional/national competence in the USA, Canada and Mexico, a not-for-profit organization for security of North American energy companies, specifies standards and requirements for information security of the energy sector
Recommendation: Use for informational purposes only to address cybersecurity of OT systems in the EU.
ANSI/ISA 62443, since 2010 (formerly ISA-99), regional/national competence in the USA, coordination of national legislation with international standards
ANSI The American National Standards Institute, since 1918
ISA The International Society for Automation, since 2007
Recommendation: Use for informational purposes only to address cybersecurity of OT systems in the EU.
IEC 62443, since 2018, international/EU competence, (also as ISA/IEC 62443), cybersecurity standards for IACS or DCS systems (adopted and completed from ANSI/ISA 62443)
IACS Industrial Automation and Control Systems
DCS Distributed Control Systems
Recommendation: Suitable for addressing cybersecurity of OT systems in the EU, the field of manufacturing industry.
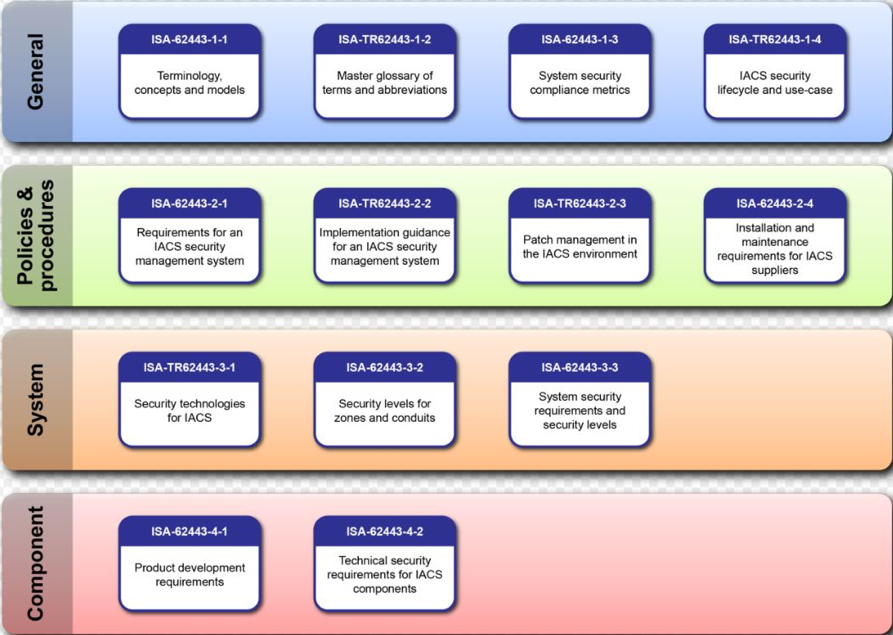
The document structure:
ISA/IEC 62443-1-x General Terminology, Policies, Cybersecurity Models
ISA/IEC 62443-2-x Process Management, Organizational Cybersecurity
- requirements for operators
ISA/IEC 62443-3-x Recommendations and Requirements from the Perspective of IACS Systems
- requirements for an integrator/contractor
ISA/IEC 62443-4-x Recommendations and Requirements from the Perspective of End Devices
- requirements for a manufacturer
ISO 27001, since 2013, international competence, (also as ISO/IEC 27001)
- describes and assesses the implementation of information security management concept in organizations
ISO – International Organization for Standardization
ISMS – Information Security Management System
Recommendation: Suitable for addressing information security within organizations in the EU, for all fields
BDEW White Paper, 7 May 2018 / 2nd updated edition, EU competence, the BDEW White Paper describes proven in practice cybersecurity concepts and solutions of defense-in-depth devices, both at the system level and at the level of individual OT components (end devices).
Recommendation: The Directive is recommended for the effective solution of cybersecurity of OT systems in the EU, for the fields of energy, transport and water.
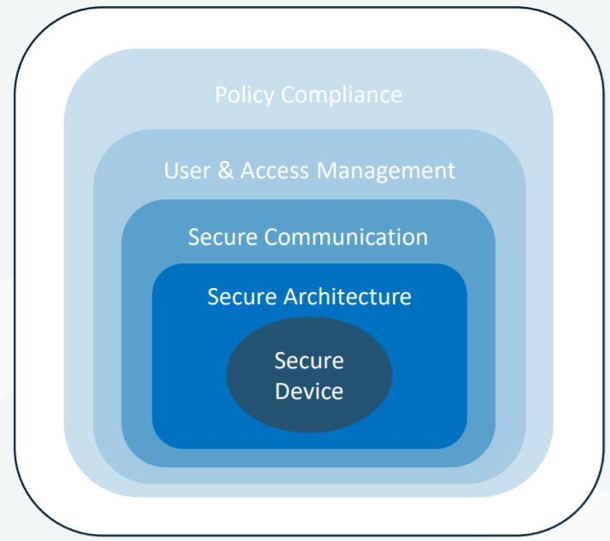
Defense-in-depth principle, the principle of a comprehensive cybersecurity solution at several levels (the “onion” principle – multiple layers of protection)
- More information in Recommendations for Energy Sector





