
Warning against attempts to penetrate the system by exploiting the ZOHO Assist platform
The National Cyber Security Centre SK-CERT warns against a large-scale phishing email campaign exploiting the ZOHO Assist remote access service to gain an unauthorised access to the system. The campaign has been running since 8 January 2022 and messages have been addressed to both private and company email addresses.
In today’s known cases, the attacker acts under the l8dfhfghfg@grand-tehno[.]ru account (the email may change over time) and sends out email invitations containing the ZOHO Assist client installation file via the “Unattended Remote Access” service. The email itself (see picture below) is generated by the attacker directly from the ZOHO Assist web administration interface and is sent from the legitimate email address [email protected]. The attacker has placed texts in various language mutations in the body of the message, trying to arouse victims’ interest in cooperation. The end of the message body contains the URL link used to download the ZOHO Assist installer configured for “unattended remote access”. The installation itself needs the standard permissions required for the installation of applications. However, once installed, the attacker can access the victim‘s device at any time, unnoticed, without any confirmation by the victim. Thus, the device is under the full control of the attacker without the victim‘s knowledge.
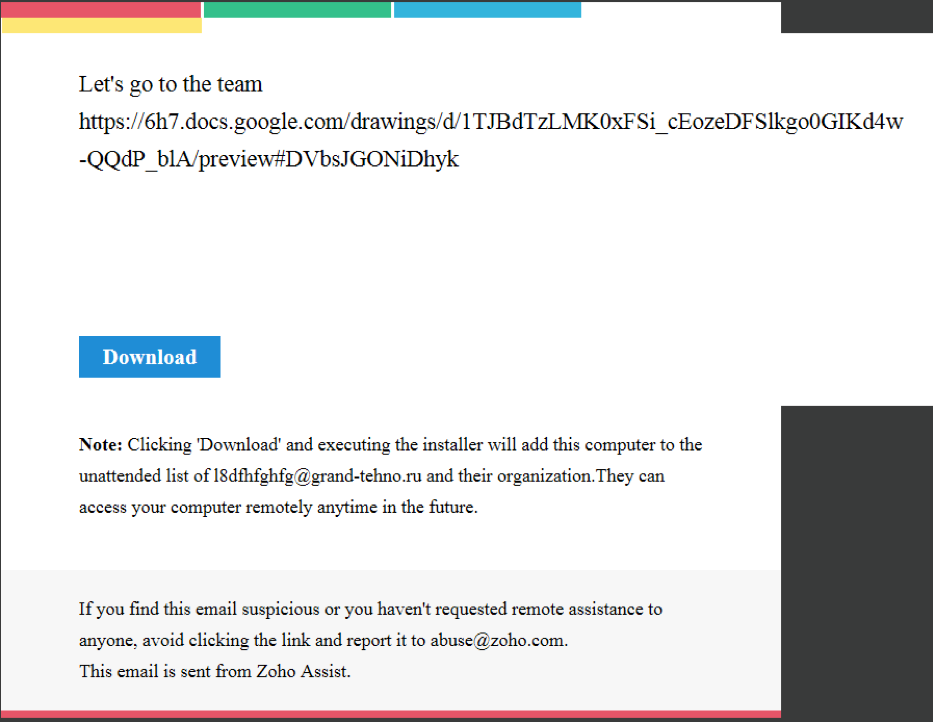
Exploiting remote access services in various phishing and scam campaigns is nothing new; they have been intensively exploited by attackers in last year’s Microsoft Tech Support Scam campaigns aimed at contacting the victim via the phone. The current campaign, exploiting ZOHO Assist service, differs in contacting potential victims by e-mail.
The National Cyber Security Centre SK-CERT recommends the following
- For users:
- do not open unverified messages and messages from unknown users
- do not open suspicious attachments (even in familiar formats such as .pdf/.docx, and so on)
- disable macros in documents
- do not open suspicious URLs
- if email applications are used, disable the attachments preview function
- in case of suspicion, verify the content of the message with the sender in a different way (by phone, in person)
- never respond to messages requesting any personal and sensitive information (login names, passwords, payment details)
- pay special attention if you notice any message on your device’s screen about installing apps on remote access or remote message
- For administrators:
- disable all remote access services and block access to these services (blocking techniques vary according to the type of a remote access service)
- allow remote access services according to individual legitimate requirements
- prevent users from installing applications individually or running unauthorised applications on their workstations
- utilize centralized deployment of any applications on workstations and servers
- minimise the use of remote access from an external environment, especially regarding important and critical services
- if remote access is used, use validated security measures such as VPN tunnels, and so on
- For managers:
- ensure briefing of employees about phishing threats
- check the remote access policy settings and take remedial action in case of inappropriate status
- check on a regular basis who and why is using remote access to the organisation’s systems
- apply appropriate access management measures
IOC
Mail:
l8dfhfghfg@grand-tehno[.]ru
URL for downloading ZOHO Assist client allowing unattended access for the attacker:
hXXps://assist.zoho[.]com/unattended?encapiKey=wSsVRa0irhKjBql7nGKtL%2BY7zQ9WVVzzRhl03FDwuXT%2FT%2
FqW88cyn0OYDQXyT%2FNLFzY6EWBBrOgumx5S0DAKj9h%2Byl1UDCiF9mqRe1U4J3x1p7rvnjDMWW1dkxOILIoMwAxjnA%3D%3D
« Späť na zoznam





