Recommendations for Energy Sector
Energy systems are one of the main components of critical infrastructure.
This part serves as a basic recommendation for all operators of essential services of all sectors/sub-sectors (such as transport, energy, industry, water, gas, oil, chemistry and metallurgy) operating energy devices.
Cyber threats are constantly evolving and introduce new ways of attacks. Statistics of cyber incidents clearly confirm that about 20% of attacks are coming from “outside” of systems and about 80% of attacks are from “inside” of systems. Actions based on organizational measures and the “human factor” appear to provide only partial and less effective cybersecurity.
An internationally accepted and tested in practice directive on addressing cybersecurity of control systems of critical infrastructure energy devices is the BDEW White Paper (2nd updated edition, 7 May 2018).
Basic principles of the cybersecurity architecture are:
- Security by design, cybersecurity functions must be an essential part of component design and development,
- Minimal need-to-know principle, cybersecurity functions must be user-friendly and shall not require a knowledge level of of administrators,
- Defense-in-depth principle, the principle of a comprehensive cybersecurity solution at several levels (the “onion” principle – multiple layers of protection),
- Redundancy principle, a basic principle of operational security ensuring that a single failure does not render the whole or a significant part of the system inoperable.
An important security requirement is to avoid “Vendor Lock-in“, i.e. dependence and reliance on one manufacturer, which might be caused by particular solutions and functionalities.
At present, the BDEW White Paper is supported by reputable manufacturers of OT devices and is implemented in European companies operating energy systems.
The BDEW White Paper describes proven in practice cybersecurity concepts and solutions both at the system level and at the level of individual components (end devices).
A reliable and proven cybersecurity principle is currently a multi-level “defense-in-depth” concept:
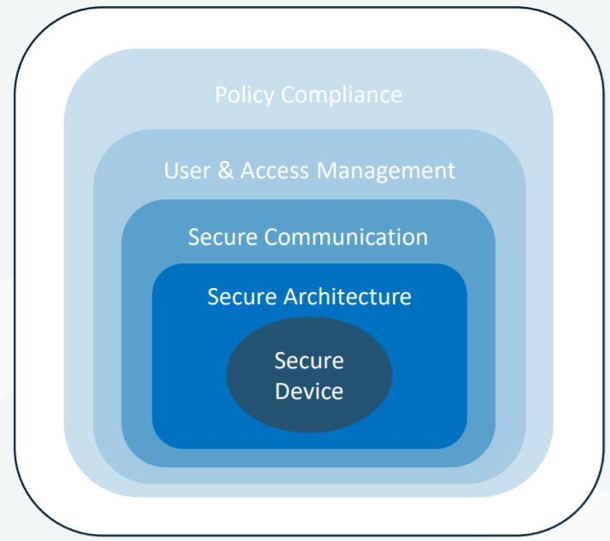 Recommendation: Minimum technical requirements for cybersecurity of OT systems, “Defense-in-depth” concept
Recommendation: Minimum technical requirements for cybersecurity of OT systems, “Defense-in-depth” concept
Minimum technical requirements for cybersecurity at the level of particular components apply to each particular OT device – an end device (containing elements such as a microprocessing unit, operating system, communication interfaces and so on).
Particular functions of active defense-in-depth cybersecurity must be implemented at hardware level and end-device operating system level.
Minimum technical requirements for functions and parameters of active and effective cybersecurity of OT devices are the following:
- function of generation of security logs (Syslog),
- secure communication through monitoring and analysing of events in network and information systems (Security Information and Event Management – SIEM) using RADIUS protocol (Remote Authentication Dial-In User Service),
- function of network management SNMP v1,2,3 (Simple Network Management Protocol),
- function of Host Firewall layer 2,3,4,7 (see the ANSI Table),
- function of Router, VLAN network segmentation (Virtual LAN),
- function of secure system access and authorization management via RBAC (Role-based Access Control) and AAA mechanism (Authentication-Authorization-Accounting),
- function of secure remote access via SSL (Secure Sockets Layer)/TLS (Transport Layer Security),
- function of communication encryption via IPSec, OpenVPN,
- function of encryption via HW Crypto-chip,
- encrypted memory/ memory protected by a certificate SSHD, SD card,
- system of active antivirus protection, IPS (Intrusion Prevention System), MAC (Mandatory Access Control),
- system of autonomous monitoring and detection of cyber incidents – IDS (Intrusion Detection System),
- provision of upgrade and support (Patch Management) by the manufacturer during the entire life cycle of the system (at least 15-20 years).
Recommendation: Organizational and procedural cybersecurity
Particular recommendations of the BDEW White Paper are also linked to the cybersecurity solution system in the organizational and procedural areas, which are in more detail covered in the international standard ISO/IEC 27001.
Minimum technical requirements for cybersecurity shall be applied and documented during all phases of the life cycle of OT device, i.e. during:
- acquisition (commercial and technical documentation for contractor selection, commercial supply contract),
- project preparation (technical implementation documentation, actual execution documentation),
- implementation (supporting technical documentation, software development, tests),
- operation (handling and operating rules, instruction manuals, training instructions),
- maintenance (service and maintenance manuals, service contract).
Recommendation: Cybersecurity measures for existing OT systems
One of the specific features of OT systems is the life cycle, which can be 15 to 20 years (in the case of IT systems it is only 4 to 6 years). So the question is, how to secure existing systems that still have most of their life cycle ahead?
Recommendation No. 1:
Technologically advanced systems based on modular hardware and software concept enable to modify, extend or update a part of the device (hardware or software modules) without the need to replace the whole device. In such case, it is recommended to contact the manufacturer to update or add a necessary hardware or software (usually it is only a processor unit), and thus fully and without much intervention solve the security issue.
Recommendation No. 2:
In case the systems used are not based on modular architecture and do not allow to modify, extend or update parts of the device, it is possible to increase the level of security by adding an additional element (hardware + software), which will perform some basic functions such as monitoring of communication network, controlled access to LAN network and devices, reporting intrusions into the system, and so on.
Recommendation No. 3
Manufacturers of OT systems offer various technical means of additional security, whether a “communication gateway” or “LAN monitoring”, and others. When selecting additional technical means, it is recommended to focus on elements and devices based on industry standards. Windows PC-based solutions, designed for office use, are not recommended.
An important note
It should be noted that the above mentioned Recommendations No. 2 and 3 are only temporary measures until the existing devices are upgraded or modernized and, on that occasion, exchanged for new technologically advanced ones containing effective protection.





